TCG Opal 2.0 Primer
The TCG Opal Security Subsystem Class (SSC) is a set of specifications for self-encrypting drives (SEDs) developed by the Trusted Computing Group (TCG), a non-profit organization that develops, defines, and promotes open standards and specifications for secure computing.
The Opal SSC, currently available in version 2.0, presents a hierarchy of security management standards to secure data from theft and tampering by unauthorized persons who are able to gain access to the storage device or host system where the storage device resides.
What are Opal 2.0-Compliant SEDs?
Self-encrypting drives (SEDs) supporting Opal 2.0 use hardware encryption technology to secure data stored in them. By encrypting the entire drive, users do not have to worry about their data being accessed if the drive, laptop or mobile device gets stolen or lost.
An Authentication Credential (which may be derived from a password, passphrase or other authentication mechanism) is used to generate a Key Encryption Key (KEK), which encrypts the Media Encryption Key (MEK) before it is stored in the SED. The MEK is generated internally in the SED and is persistently stored in encrypted form; its plain text is kept only within the SED controller and only while the SED has power. When the SED no longer has power, the MEK plain text is lost, rendering the drive “locked.”
Upon power on, the user supplies a password, passphrase or other authentication mechanism, from which the host application generates an Authentication Credential. This credential is then sent to the SED to unlock the drive and provide access to the data. If the credential provided is correct, a Key Encryption Key (KEK) decrypts the encrypted MEK, which can then encrypt/decrypt data.
According to a joint whitepaper released by the Trusted Computing Group and NVMe Express, storage devices implementing Opal “are built to protect the confidentiality of stored user ‘Data at Rest’ (DAR) against unauthorized access once it leaves the owner’s control, when or after the storage device has been power cycled.”
Advantages of Opal 2.0-Compliant ATP SATA & NVMe™ Drives
ATP’s next generation SATA and NVMe drives comply with the Opal 2.0 standard, ensuring a secure layer of protection for data at rest. These SEDs offer several benefits and advantages over software-based encryption:
- No Performance Degradation. In contrast to software encryption, hardware encryption frees the CPU or operating system from the load of the encryption/decryption process, so there is no degradation in overall performance.
- OS-Independent Security. Attackers can exploit vulnerabilities in the operating system by executing malicious code. SEDs perform encryption within the drive controller and do not store encryption keys in the host processor or memory, which can be attacked by hackers. Additionally, user authentication is performed within the SED before the drive is unlocked, so threats coming through the OS will not work.
- Encryption Management-Free Protection. SEDs automatically generate the Media Encryption Key (MEK) internally and therefore does not require encryption key management. The self-generated key stays with the drive, making stored data inaccessible even if the drive is stolen or lost. Data can be read from and written to the SED only after the correct key has been supplied.
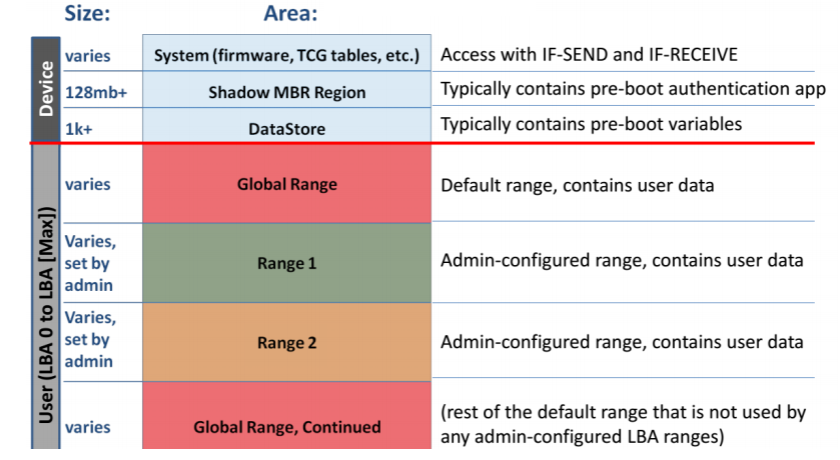
Figure 2. Opal Device layout: The user area is always encrypted with a Media Encryption Key (MEK). The MEK is encrypted/decrypted with a Key Encryption Key (KEK). The user area may be subdivided into different zones with different keys, locked/unlocked and cryptographically erased independently from others, and may have different users assigned with lock/unlock permissions). (Image reference/source: Trusted Computing Group and NVM Express Joint White Paper: TCG Storage, Opal, and NVMe)
Security Features
Opal 2.0-compliant storage devices come with the following features:
- Encryption: Hardware encryption of user data supporting AES-128/256 standard (no user interaction required).
- Credentials: Provisioning and configuration using Admin credential; support for multiple user credentials, which can be assigned to perform various actions.
- Locking Ranges: The storage device may be subdivided into multiple "Locking Ranges," each of which is a range of contiguous logical block addresses (LBAs). Each Locking Range may be encrypted with a different MEK and may be unlocked independently of others. Permission to unlock Locking Ranges may be assigned to zero or more users.
- Cryptographic Erase. This refers to the process of destroying a MEK and generating a new one, which means that the data encrypted with that MEK can no longer be decrypted. Locking Ranges may be cryptographically erased independently of the others. Permission to cryptographically erase Locking Ranges may be assigned to zero or more users, providing a fast and secure way to repurpose the drive or perform end-of-life operations. This feature is available as part of ATP’s SecurWipe featureset.
- Master Boot Record (MBR) Shadowing Support. The host application can store and execute a “Pre-Boot Authentication (PBA) Environment” to unlock the range in which the OS is stored so that the OS can boot.
ATP SecurStor: Protection Beyond Opal and AES
An Opal-compliant SED offers several advantages in effectively preventing unauthorized data access due to the loss or theft of the drive or a system that integrates the drive. However, it is not designed to protect data from a breach that occurs after the drive has been unlocked with valid authentication credentials with the OS and applications already launched. If the authorized user has not yet been de-authenticated by the system through a power cycle, the drive remains vulnerable and therefore requires other security mechanisms to keep it protected from unauthorized access.
ATP SecurStor provides a multi-level security suite that protects data with a variety of options beyond data-at-rest encryption and pre-boot authentication. Customers can choose from features that can be customized according to their application-specific requirements to guard against unauthorized access, illegal copying and other security threats to ensure data, OS and firmware integrity at all times.



